Why Use Cryptography?
Alice wants to send the message to Bob “Attack at Dawn!”. If Eve were able to intercept this message, Eve would know that an attack is coming at dawn and could prepare. So Alice wants to encrypt the message so that only Bob can read its contents. This is an example of a basic problem that can be solved with Cryptography.
What is Cryptography?
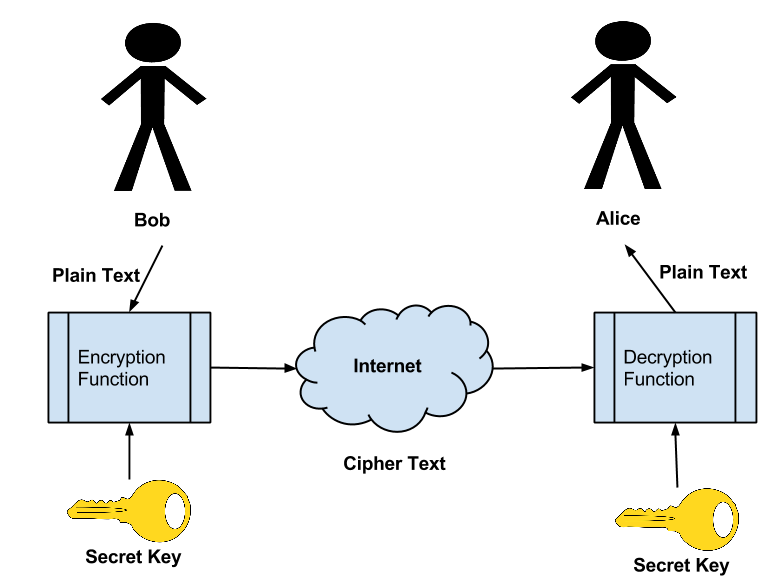
Cryptography is the act of changing a message such that the contents of the message are unable to be determined by an observer with out the knowledge of what the shared secret is (e.g., the Key).
Cryptography also requires that the original message contents are able to be easily produced from the Encrypted Message if the Key is known. Encryption allows Bob to send his Secret Message “Attack at Dawn!” to Alice over an non secured channel such as the internet.
History of Cryptography
Caesar Cipher (Shift Cipher)
One of the earliest known encryption techniques is the Caesar. Â The Caesar Cipher also known as the Shift Cipher is an encryption scheme where letters in the message are replaced by another letter at some fixed distance away.
Vigenere Cipher
The Vigenere Cipher is an encryption method which uses a series of Cesar Ciphers (Shift Ciphers) to encrypt letters of an alphabet.
Substitution Cipher
The Substitution Cipher is different from the Caesar and Vigenere Cipher in that it does not shift alphabetic letters, rather it substitutes them for another character entirely. A could map to J while B could map to C.
Asymmetric Cryptography
Public Private Key Cryptography is also known as Asymmetric Cryptography is where 2 keys are utilized. One key for encryption and on key for decryption. Asymmetric cryptography is at the core of digital signatures.
Why Do we need Public / Private Key Cryptography
In Traditional Symmetric Key Cryptography the keys for encryption and decryption must be shared before any secure communications could take place. This means a secure channel, often via sneaker net, was required to share key material. In the modern world of the internet it is impossible to establish a trusted channel before communication can take place. This is where Public / Private (Asymmetric) cryptography come in.
Lets first take an example. Bob wants to send a secret message to Alice. Bob uses Alice’s Public Key and an Asymmetric Encryption Algorithm to encrypt the message. At this point only Alice’s Private Key can decrypt the message. Bob sends the Cipher text to Alice and Alice uses her Private key, known only to her to decrypt Bob’s message. Â The following figure shows an example of the transaction.\
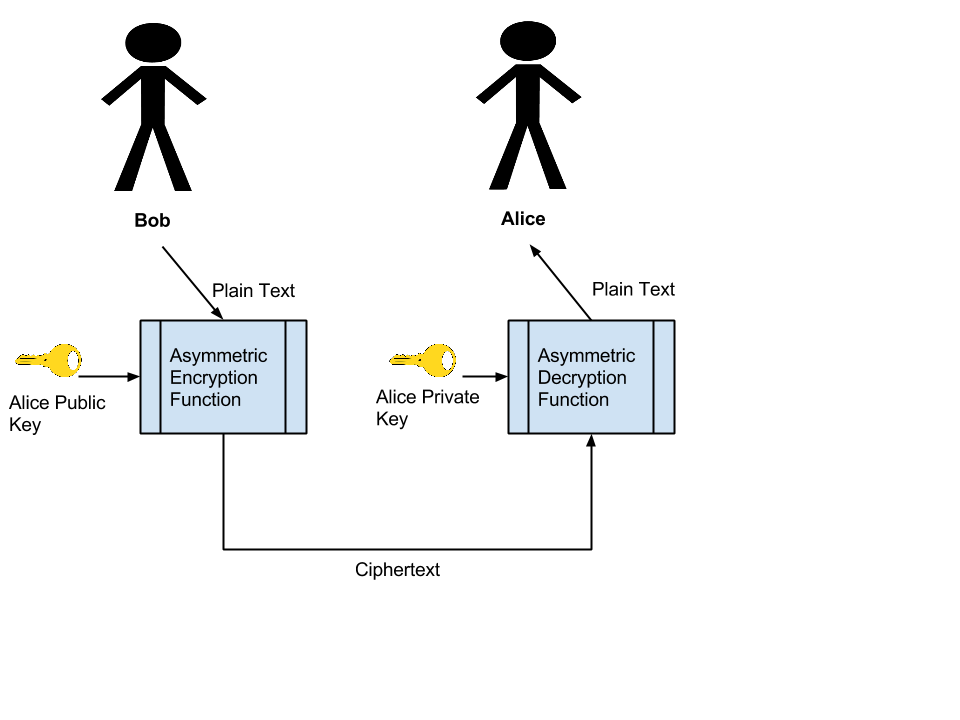
When Alice wants to send a message back to Bob the process is simply reversed. Alice, using Bob’s Public Key, encrypts the message. Bob will than use his Private Key to decrypt the message contents.
Disadvantages of Asymmetric Cryptography
Asymmetric Cryptography Algorithms are far slower than Symmetric Algorithms as well as limited in the amount of data that can be encrypted. Â This is because when the RSA Asymmetric algorithm is used, the length of the message must be smaller the the modulus. Â Typically Asymmetric algorithms are only used to encrypt a symmetric key, which is used for the remainder of the encryption.
Additional Problems
Asymmetric Cryptography is used in the security of the internet to verify the publisher of the content and to provide a means for Symmetric Key exchange. In a typical SSL/TLS Internet connection the Server you are connecting with provides you with its Public Key. The problem arises in verification that it is the correct public key and belongs to the server you are intending to communicate with. For more information on how this verification takes place, check out Public Key Infrastructure (PKI)