What is a Digital Signature?
A Digital Signature, much like a handwritten signature, is intended to provide an assurance that the message was signed and sent by the claimed sender. Digital Signatures are often based on Asymmetric Cryptography, and hashing algorithms where the Private Key is used to Sign a hash of the information. The recipient of the information will than re-compute the hash of the received content, decrypt the hash with the public key of the sender and compare the two. If the decrypted hash value matches the recomputed hash value the receiver has a level of confidence that the message originated from the sender and not a third party.
A Digital Signature Example
Suppose Bob wants to send a signed message to Alice. Â Bob takes his message, and runs it through a Hashing Algorithm (such as SHA-1 or SHA-2) to produce a message hash. Bob uses an Asymmetric Cryptography Algorithm and his Private Key, known only to Bob. Bob encrypts the message hash with his private key and appends it to the original message. Â Bob will optionally attach his Public Key to the message and send the contents to Alice as shown.
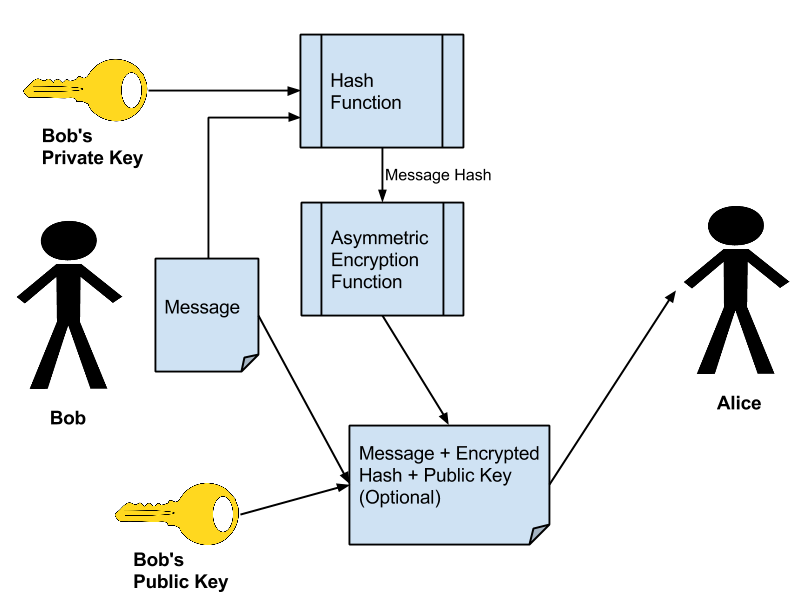
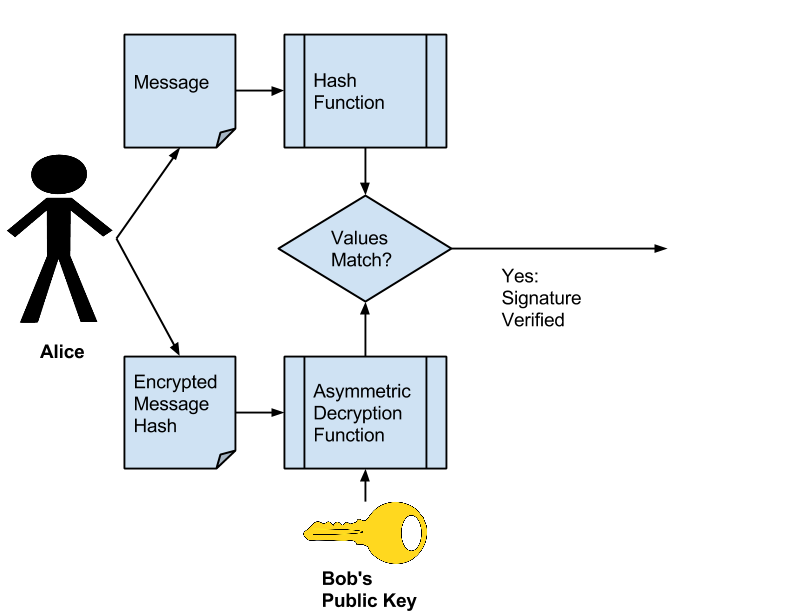
When Alice receives the message, Alice can verify the contents by first re-computing the message Hash value by running the message contents through the same Hash algorithm that Bob used. Second, Alice uses Bob’s Public Key to decrypt the message hash that Bob previously calculated. If the two hash values match Alice knows that it was Bob who sent the message. The message verification process is shown in the following figure.
Important Note: The previous scenario makes two very important assumptions.
1.) Alice independently verified Bob’s Public Key before using it.
2.) The message contents had some form of Unique Identifier to prevent replay attacks.
First, lets examine why Alice needs to verify the Public Key before use. If Alice does not verify the message is signed by Bob’s actual public Key anybody can send a Key along with a signed message and claim to be Bob. To Solve this problem a Public Key Infrastructure was established.
Second, lets examine why the message requires a Unique Identifier. Let us assume that Bob sends the signed message to Alice as normal, but instead of only going to Alice the message is also intercepted by Eve. Eve can than replay the message at a later time and Alice would still assume that it came from Bob. This is because the message that Eve sent was a valid signed message. Let us take a more concrete example. Lets pretend that Bob is a banking Client and Alice is the Bank. Bob sends a signed message to Alice saying transfer $10,000 to Eve. Eve intercepts this message and replays it and is able to tell the Alice to keep transferring funds even when it is not Bob sending the message